Invisible Data is Risky Data
Unprotected PII and Hidden, Unsecured Files Need Identification
Manage Risk with D3 Data Identification, Categorization & Monitoring
Why Is a Data-Centric Approach Important to Data Security & Compliance?
Data breaches are increasing with ransomware attacks and the White House is urging organizations to take measures like data backup and testing response procedures. However, it may be impossible to completely prevent an attack, which is why a data-centric approach to security is critical.
Humans make mistakes in securing data, sometimes in error or out of convenience in the moment. Employee turnover causes risky files to be inherited without management of those files. IT staff often are not in a position to make a decision about what to delete.
These untracked gigabytes of potentially sensitive files with PII, passwords or noncompliant data create a hazard for organizations. Compounding the problem is DROT (Duplicated, Redundant, Obsolete, Trivial) files that take up expensive and unstructured space in data storage.
Our partner, NowVertical, found from their research, that every organization may hold as much as 10 GB of unstructured DROT data per employee. And on average, 42% of this data is company sensitive and should be encrypted, protected or deleted before cloud migration, with 1% of files even containing security risks like passwords in plain text with encryption keys alongside databases.
A single, small mistake can lead to serious reputational and financial damage to an organization, and there are plenty of examples already in the news. Without knowing what you have, you can’t know what needs to be protected, deleted or remediated prior to migration.
But there is a solution. Bring all your data into the light so you can respond responsibly.
Mitigate Data Risk Responsibly with Data Visibility
Anacomp’s data visibility and digital transformation solutions enable comprehensive indexing via content, source and attribute mapping for all of your data risk, data migration and compliance management.
Our services and software include digitization, AI/machine learning and OCR content extraction, automated indexing of high-volume petabytes of files with customizable metadata, federated search for compliance and regulatory requests, and a continuously updated, drill-down inventory of digital files with notifications for interdepartmental management.
Data Digitization & Risk Assessment Solutions

Discovery & Classification for Compliance
D3 is the only solution that solves the problem of automated data estate inventory and identification, with customizable metadata assignment for all records based on actual content, context and data source location.
Features
- High-Volume, Continuous Data Crawling Using Machine Learning & Auto Indexing
- Powerful, Customizable Metadata Based on File Attributes, File Content & Context
- Classification of Files and Bulk Tagging for Records Management Control
- Integration to Common Data Sources & APIs for Analytics, Security and Records
- User-Friendly Dashboard UX Visibility & Click-to-Content, Drill-Down Detail

High-Volume Record Digitization
If the agency has physical records and desires digitization, Anacomp provides high-quality digitization services of paper, micrographic and large format drawings with associated metadata to facilitate search, retrieval and records management.
Anacomp offers turnkey solutions to Federal agencies for the digitization of official records with implementation in days, not months.
Secure Records Control
Complete physical and electronic chain of custody management is delivered through Anacomp’s proprietary document and production control systems.
- NIST SP 800-171
- NIST SP 800-53 Level 3
- OMB Circular A-130
- The Privacy Act of 1974
- HIPAA

RIM Professional Consulting Services
Anacomp is a leading U.S. provider of RIM (Record & Information Management) consulting services and engagement offering an actionable plan for record management, including high-volume digitization of records.
Experience
We have developed a proven, highly developed and refined holistic methodology to evaluate records management systems and streamline transition from paper-based to electronic records processes.
Assessment
- Physical Records
- Unstructured Data
- Compliance Gap Analysis
Deliverables
- Documentation & Analysis of Current Processes
- Recommended “To Be” Process State
- Cost Benefits Analysis & ROI
The scope may also include assessment of the company’s electronic file shares and recommendations for digitization or archival storage of physical records.
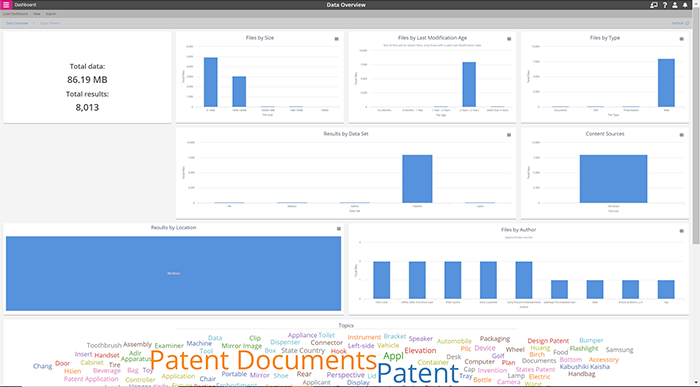
The example above shows a drill down on “patent” in the previous menu word cloud. Metadata is customizable and some of the typical metadata include:
- File Content
- Date of Creation & Last Modified
- File Size
- Author
- Document Type
- File Location Path
Identify High Risk Items in Your Data Estate with Drill-Down Accuracy
Solutions for All Your Digital Data Challenges
Data Security & Privacy Challenges
Data identification down to the content level to assign role-based security to unstructured file shares
High volumes of potentially unprotected texts, emails and other unstructured data
PII data duplicated and unprotected in multiple data sources
D3 can help you identify, assess and secure your data with confidence
Access to Entire Data Estate for Analytics Challenges
More than 80% of data assets will be unstructured by 2025 according to IDC's 2018 report
Limited visibility of unstructured data, role-based management of files and personnel interactions limits analytics accuracy
D3 can help you capture, analyze and harvest value from your data estate with confidence
FOIA & Declassification Challenges
Increasing regulation including FOIA, HIPAA and other regulations require ongoing and timely PII management
Over-retention risk monitoring while maintaining compliance with data retention requirements
Unknown or unidentified PII data within unstructured data that require application of appropriate security controls
Fines and reputation risk from data breach or non-compliance
WorkSmart & D3 can help you manage your entire data estate with proper controls and data compliance with confidence
Cloud & Data Migration Challenges
Lack of visibility of ROT (Redundant, Obsolete, Trivial) data
Inability to properly classify and merge data sources
Exposure to security risks and ransomware
Interdepartmental review and assignment of data for migration and systems integration
D3 gives you a holistic view of your entire data estate so you can assess and manage risk and ROT and assign role-based security with confidence
